We started Apple Security Bounty with one steadfast goal: to recognize and reward the security community for sharing research with us to help protect our users. We invited a small group of researchers to join the program when it launched in 2016, and we received so many helpful submissions that we opened it to all researchers in late 2019. Today we’d like to share our first update on our progress and the improvements we’ve made, many based on feedback from researchers, as we continue to work on this important mission.
In the past two and a half years since opening our program, we’re incredibly proud to have awarded researchers nearly $20 million in total payments, with an average payout of $40,000 in the Product category, and including 20 separate rewards over $100,000 for high-impact issues. To our knowledge, this makes Apple Security Bounty the fastest-growing bounty program in industry history.
During this time, our team has worked closely with researchers around the world, and we’ve learned about some things we can do better.
First, we’re responding much more quickly. At times we received many more submissions than we anticipated, so we’ve grown our team and worked hard to be able to complete an initial evaluation of nearly every report we receive within two weeks, and most within six days.
Next, we’re making it easier for researchers to report issues and communicate with our teams. Our Apple Security Research site includes a new way to send us research on the web and get real-time status updates. Just sign in with your Apple ID and follow the prompts to send us a detailed report. You can then track the progress of your report and communicate securely with Apple engineers as we investigate.
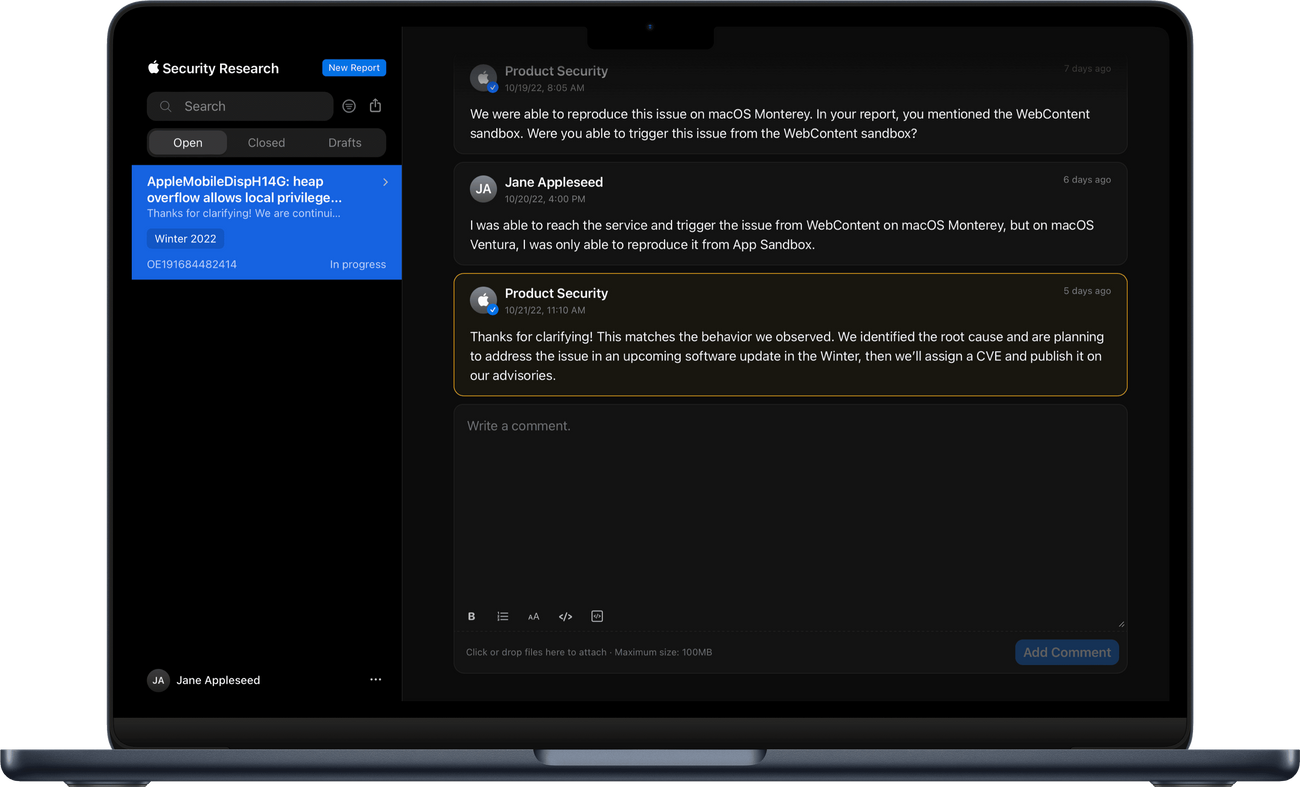
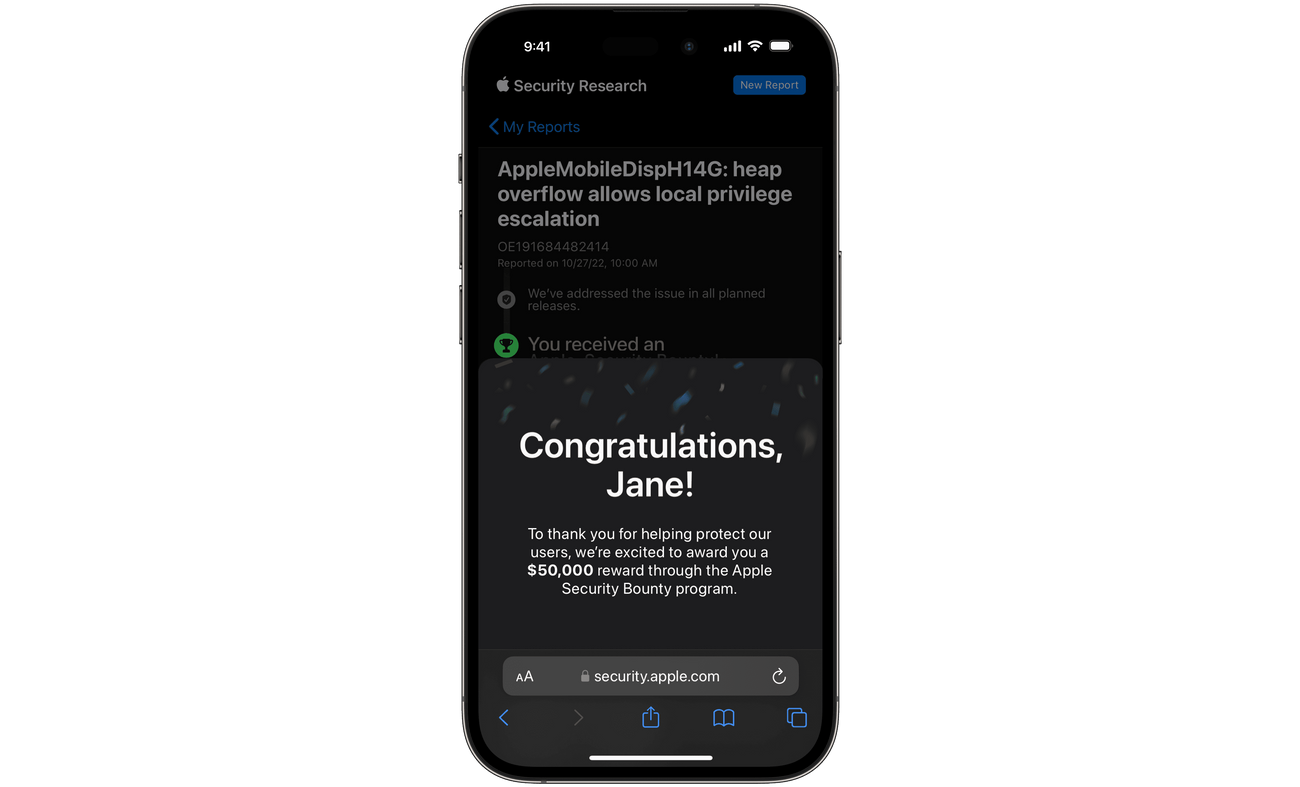
Anytime there’s a change to the status of your report, it’s immediately reflected in the new tracker. If we have a specific update or need more information, you’ll also get an email notification. And if we make changes to the security of our devices or services based on your report, we’ll keep you up to date on the details, and let you decide how you’d like us to credit your work. We evaluate all eligible reports for Apple Security Bounty, and if your report receives a reward, we’ll notify you right away — both in the tracker and by email.
We’re also providing more transparency. Our site now includes detailed Apple Security Bounty information and evaluation criteria. Bounty categories include ranges and examples, so you can determine where you’d like to focus your research, and so you can anticipate whether your report qualifies for a particular reward. We’ve provided ranges for submissions that impact Apple services and infrastructure, as well as our products.
Starting today through November 30, 2022, we’re also accepting applications for the 2023 Apple Security Research Device Program. This program features an iPhone exclusively dedicated to security research, and can help you get started, go deeper, or improve the efficiency of your research work with iOS.
Thank you for all your contributions to Apple security research and for helping us protect the users of over 1.8 billion devices around the world. With your support and feedback, we’ll keep working to make our security research programs the best in the industry. We have much more planned for the coming year, including an expanded research scope for Apple Security Bounty and other program enhancements. Along the way, we’ll share program updates—as well as unprecedented technical detail about some of our most important security engineering work—right here on this site. And we start today, with a post on critical memory safety improvements we’ve made in the XNU kernel.